Cybertext Killed the Hypertext Star
Nick Montfort reviews Espen J. Aarseth's Cybertext, which stakes out a post-hypertextual terrain for literary criticism and practice. Interactive excerpts from some of the cybertexts that Aarseth discusses are included.
the hypertext murder case
“Hypertext is dead - ” declared Markku Eskelinen at Digital Arts and Culture ‘99 in Atlanta. “Cybertext killed it.”1 No doubt, interesting hypertext poetry and fiction remains to be written, but - if we consider hypertext as a category that defines a special, valid space for authorship and criticism of computerized works of writing - Eskelinen is clearly right. The hypertext corpus has been produced; if it is to be resurrected, it will only be as part of a patchwork that includes other types of literary machines.
One viable category today, perhaps the most interesting one to consider, is that of “cybertext.” The word was first used in the critical discourse by Espen Aarseth in Cybertext: Perspectives on Ergodic Literature. The term denotes not all possible networks of lexia, but the more general set of text machines. These machines are operated by readers, and depending upon how they are operated they present different outputs, different texts for reading. The cybertext category therefore contains hypertext, which is operated by means of clicking and traversing links, but it is much broader. Indeed, Aarseth’s chief accomplishment in Cybertext was not to completely illuminate any particular interactive work or form of computational writing, but to erase the stifling hypertext boundary, and to redraw that boundary so that it demarcates a more interesting territory of reader-influenced texts. The cybertext terrain includes computational literary artifacts that are in some cases novel, although yet to be thoroughly explored. In other cases, the cybertexts included have some history, but one that is woefully neglected.
Notably absent from Aarseth’s definition of cybertext is mention of the link, and this missing link - or, more specifically, this replacement of the link with a more interesting feature of computational literary interaction - frees the new category from the chains of a critical-theory-influenced and essentially non-computational perspective. The definition of computer hypertext given in George Landow’s 1992 Hypertext (a work that, like Cybertext, took the category of literature under consideration as its eponym) was drawn from Roland Barthes’s S/Z. Landow describes the form as “text composed of blocks of words (or images) linked electronically by multiple paths, chains, or trails in an open-ended, perpetually unfinished textuality described by the terms link, node, network, web, and path.” Landow also indicates here, by his use of the term “computer hypertext,” that non-computer hypertext - besides the hypertexts he describes as implicit, such as Ulysses - exists as well; Cortázar’s Hopscotch and Queneau’s “Story as You Like It” are in this category. Oddly, the idea that hypertexts can appear in print has been a contentious point for some critics, many of whom either see the electronic digital computer as an essential element in defining a category of interactive texts or consider all texts (which one can, after all, skip around in) as hypertexts. Aarseth deftly disposes of this issue by simply making his definition independent of the medium in which the work is presented.
As appropriate as the hypertext category might be for Landow’s topic (the embodiment of late 20th century critical theory in interactive computer text forms), it includes only a subset of electronic literary efforts. An extended analogy to the theory of computation demonstrates this restricted scope, and explains why the old collection called hypertext cannot continue to hold our interest as a critical category or as a category describing what literary efforts should be considered valid and worthy.
classes of computational power
There are four different classes of theoretical computers. Since theoretical computers can compute the same sorts of algorithms as can languages governed by formally-defined grammars, these four computational classes map directly to four classes of formal language. Only the first and fourth class will be considered at all here, but in terms of increasing generality (i.e., ability to execute larger and larger sets of algorithms to solve additional classes of problems) the four classes are as follows, ranked in what is known as the Chomsky hierarchy:
- Finite automata / Regular languages
- Pushdown automata / Context-free languages
- Linear bounded automata / Context-sensitive languages
- Turing machines / Recursively enumerable languages
A computer in the first class, when given a string of inputs, will indicate after each whether it accepts the input or not. Using the alphabet of possible inputs (the alphabet “ab” is one, but any alphabet, including ours, can be used) a finite automaton accomplishes useful computational tasks by accepting certain strings and rejecting others. Given that there are a finite number of words in the English language, including their inflected forms, a finite automaton using the “a-z” alphabet can be constructed to distinguish English words from other strings of letters. A large amount of enumeration would be involved, but the task could clearly be accomplished. Another automaton using the alphabet “ab” could be constructed to distinguish all strings [ab]* (which includes “abab” and “ababababab”), or b*[aaa]b* (which includes “aaabbbbbbb” and “bbaaab”), or - as the Chomsky hierarchy above indicates - any given “regular expression” of the sort Unix grep is used to find. In fact, it is correct to conceptualize the use of the Unix grep utility, or the Find dialog in Microsoft Word or one’s text editor of choice, as a way of programming a finite automaton. The programming is done so that strings in a regular language can be recognized; so the expression can be found in the text that is used as input for this simple computer. Of course, while the Find dialog is useful, it does not constitute a very powerful computer, and certainly not a general-purpose one. A finite automaton of this weakest class cannot even distinguish strings such as “aaaabbbb” and “aaaaaabbbbbb” (N occurrences of “a” followed by N occurrences of “b”) from those that do not fit this pattern. For this, a computer of at least the second class is needed.
Before leaving the finite automaton, however, it is important to note that this simplest theoretical computer can be described in a diagram that has nodes linked by transition rules. The diagram shown below describes a finite automaton that accepts strings of the form [b]*a[b]*a - any number of “b’s” (including 0) followed by “a” followed by any number of “b’s”(including 0) followed by “a.”
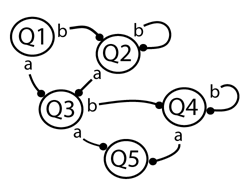
Note that the possible paths through a static Web site with five pages, each offering at most two sorts of link, can be conceptualized with a very similar diagram - with the same diagram, in fact, appropriately labeled. Hypertexts of the sort that typify the category - whether crafted in HTML or various proprietary environments such as the Microsoft Help Workshop or Eastgate’s Storyspace - present lexia (pages) as nodes, and links as transition rules. Such hypertexts are text machines of the first class, finite automata. Adding random effects, revealing or concealing links based on the history of interaction, or allowing the reader to jump to a node by name, will of course move the hypertext beyond this simplest level of computational complexity. But the essential definition of the form, a set of lexia connected by links, most clearly relates to the lowest and simplest level of the Chomsky hierarchy.
The computers sitting on our desks, stashed in our backpacks, and integrated into our cars and microwaves are (except for the non-theoretical fact that they have limited memory) Turing machines, devices of the fourth computational class. These general-purpose computing machines take input, provide output, and can solve any computer-solvable problem. Given inputs from the keyboard in the form of a string and allowing outputs to the monitor in the form of a string, a Turing machine can run Quake III, display GRAMMATRON, or beat Garry Kasparov in chess. Indeed, the computers that do these things are Turing machines. Computers may be slower or faster, and they are all ultimately constrained by disk space and RAM, but there is no known theoretical computer more powerful than a Turing machine. Because of its ability to compute any algorithmm that is computable at all, the Turing machine is also called a universal computer.
The cybertext, according to Aarseth, is a machine for the production of expression. It may model a world underneath the textual surface (as is done in MUDs and text adventures), it may select conversational responses based on the reader’s textual input (as Eliza and Racter do), or it may (as in hypertext) offer additional lexia based on the links that the reader follows. The defining characteristic of these text machines - what distinguishes them from Ulysses, for instance, however allusive and open to sampling that text might be - is that they calculate. They do not, essentially, have links. They essentially have computational ability. The paradigm of the hypertext is the least powerful computational machine, the finite automaton. The prototypical cybertext is of the fourth and most powerful computational class - a Turing machine.
hot, ergodic cybertext
“Ergodics” and “cybertext” provoke curiosity. Aarseth attracts the reading eye by using one neologism each for title and subtitle. He has also selected terms that sound somewhat similar to the words “erotics” and “cybersex.” Cybertext is certainly a recent term, and new to literary studies, but Aarseth was not the first to use it. A book by science-fiction poet Bruce Boston, published in 1992, is titled Cybertexts. The term “ergodic” is used to denote a work that requires labor from the reader to create a path. This is not in reference to a traditional book that is difficult to read, of course. Aarseth is careful not to get wrapped up in metaphorically applying the idea of multiple paths, confusing reader response for influence over the actually presented appearance of the text, or employing Barthian uses of the term “writerly” to refer to someone who is not literally doing writing. Calvino’s If on a Winter’s Night a Traveller is not an ergodic work by his definition, since, whatever tortuous paths may be represented within it, there is only one course through it that is actually presented for the reader to take. Cortázar’s Hopscotch is ergodic, by contrast, since the reader does choose a path - even though only one choice is explicitly presented, so there are actually only two explicit paths through the novel. “Ergodic” is borrowed by Aarseth from the field of ergodic theory, where it means something else entirely. The present use of the term is justified by the etymological roots of the word, which are in the Greek words for “work” and “path.”
The text that constitutes a cybertext is not “a chain of signifiers” in the linguistic sense, Aarseth explains, but “a whole range of phenomena, from short poems to complex computer programs and databases.” Text includes natural human language, but also data structures, functions, procedures, and programmatic objects. The cybertext is considered as a machine, “not metaphorically but as a mechanical device for the production and consumption of verbal signs.” The text/machine operates on verbal signs, requires a medium (just as a filmstrip requires a projector), and depends upon the action of a human operator. These three elements are shown at the vertices of the text/machine triangle. This division clarifies several confusions - pointing out that we should attend to the medium as an important but distinct aspect of cybertextual experience, and suggesting that “operation” should be considered as fundamentally different than “reading,” which of course it is.
text adventures and interactive fiction
In Cybertext there is examination of the aesthetics of hypertext, the experience of MUDs (environments that have received a good deal of attention from the perspective of cultural studies and computer mediated communication), the semiotics of an arcade-style computer game (a form seldom discussed even by game designers, which so far lacks even a critical vocabulary), and the nature of the “cyborg author” and *Eliza-*descendent Racter (representative of an underexplored form, but one that has benefited from the examination and development done by Janet Murray). These discussions are useful, although not strikingly insightful. The chapter on MUDs, for instance, does not convincingly describe these environments as mainly literary, mainly ludic, or even mainly dramatic, rather than being essentially social. The discussion of Dark Castle and Lemmings effectively topples Peter Bøgh Anderson’s semiotic typology of the computer video game, but leaves open the question of what typology might work, or whether the perspective of distinguishing classes of signs is a fruitful one at all. (Aarseth’s discussion of the typology of texts, in which he distinguishes seven variables that apply to cybertexts, is one positive contribution along these lines.) In venturing into new territory, Aarseth points out areas of interest where future work can profitably be done.
The chapter exploring Marc Blank’s Deadline, a work of interactive fiction from 1982, is particularly interesting - interesting to me, no doubt, because I work in this particular form. Aside from that, the chapter is unusual in considering interactive fiction in the context of literature. Such discussion has been almost entirely neglected by academics since Mary Ann Buckles’s 1985 PhD thesis on Adventure. Also interesting is that in this chapter, a cybertext with evident narrative elements is explored - not the case during the discussion of MUDs and arcade games. These factors make it fruitful to look at the “Intrigue and Discourse in the Adventure Game” chapter in detail. The chapter also illustrates some of the practical difficulties involved in broadening the category of acceptable electronic literature to include other works, and reveals some of the benefits and insights which can come from such broadening - insights which would have been much harder to come by if critical discussion were restricted to hypertext.
The publisher of Deadline was the software development company Infocom (now a label of Activision), which also published Zork I-III and two works that attracted some notice for their literary merits, Brian Moriarity’s Trinity and Steven Meretzky’s A Mind Forever Voyaging. The Zork series, based on a mainframe implementation of Zork at MIT, became the most widely-known commercial text adventure trilogy. It was strongly influenced by the earlier mainframe work Adventure.
Interactive fiction of the text adventure sort accepts textual, natural-language input from the individual formerly known as the reader. (Aarseth more aptly labels this individual the “operator.” I and others have used the term “interactor” in the past. Both terms suffice to show that manipulation of the cybertext is done by this individual, not just reading.) In response to this input, usually a command to the main character in the story, actions and events transpire in a simulated world and text is produced to indicate what has happened. Then, unless the character has progressed to some conclusion of the story, the operator is allowed to provide more input and the cycle continues.
The phrase “interactive fiction” is used almost exclusively today among aficionados of this form (often it is abbreviated “IF”), but this term can cause loud gnashing of teeth among hypertext authors. They ask, “if these things are interactive fiction, what is my work - not interactive?” (This complaint usually comes from the people who brought you “serious hypertext,” a phrase that clearly suggests everything else is not serious.) This would be a reasonable question in many cases, but literary terms often employ adjectives that are not exclusively descriptive of a single form. One could ask a similar question about many other literary categories, after all: “If this is concrete poetry, what is my poetry, abstract?” “If this is language poetry, what is my poetry, not language?” “If this is a novel, what is my work, a passé?” The term “interactive fiction” is not a claim that the form it describes is the only fiction that is interactive in any way. It was simply coined because interactivity and fiction are central features of this form, which also has other distinguishing characteristics that do not lend themselves to encapsulation in two words.
The other main argument against use of the term is brought up by Aarseth, who correctly points out that the word “interactive” is a commercial catchword that has been used to promise vague technological enhancements and improvements. (Ironically, of course, Aarseth names his own category of literature “cybertext” - as if the “cyber” prefix were somehow less tainted by hype than is the word “interactive.”) “Interactive” is certainly no longer constantly denuded of meaning in the marketplace today, whatever false promises it may have once held out. Historically, that word, by itself, has been used to distinguish computer processes which reply to user input (just as interactive fiction does) from batch processes, which run without any user intervention. Used in that sense, of course, the term “interactive” is very broad, and would apply to hypertext fiction as well as many other programs. But the entire term “interactive fiction” has its own history. It was used by Adventure International, and later Infocom, to designate their works, referring to something of exactly the sort described above. The term has also been used in the academic discourse, specifically to refer to works similar to Deadline since the early 1980s.
There is another reason to prefer the term “interactive fiction” over “text adventure.” Not all interactive fiction, and not even all classic works in the form, are actually text adventures, simply because not all of them are “adventures” - extraordinary explorations involving danger. In fact, Deadline is not a text adventure. Deadline is a detective mystery, in contrast to the fantasy adventures in the Zork series and the Infocom adventures that transpire in modern-day settings, such as Cutthroats by Michael Berlyn and Jerry Wolper and Infidel by Berlyn. Although interviewing murder suspects may be unusual for the interactor and may involve some danger to the protagonist, the situation is a very ordinary one for this main character, a detective. Most other famous interactive fiction works (including the very literary Mindwheel by Robert Pinsky) are true text adventures, so it is not the case that all text adventures are pulp and all other interactive fiction works are artifacts of high culture. It is the case, however, that the category “interactive fiction” is not synonymous with “text adventure,” and the former term is the appropriate one to define the whole category. Similar arguments can be made against other proposed terms, namely “text adventure game” and “text game.” Some works of interactive fiction, in addition to not being adventures, are not games - certainly, they are no more games than are the least game-like hypertext fictions. And there are all-text games, like Rogue and NetHack, which are not interactive fictions. The term “interactive fiction,” most widely used by those who actually create and experience these works, is the best descriptor for this category, and deserves to be re-established as interest in this form is reawakened.
Discussion of terminology may appear to be useless quibbling, but it is very important if new types of ergodic literature are to be considered by hypertext authors and critics. It is very difficult for individuals to take some alien subcategory of the cybertext set seriously if they disagree vehemently about what that category should be called. If they happen to strongly prefer a name that sounds low-cultural and non-literary, it is all the more important to advance solid arguments for the commonly used and most precise term.
meeting deadline
Aarseth examines “adventure game” interaction as exemplified by the murder mystery Deadline. In this interactive fiction cybertext, both story and game, Mr. Robner has been found dead in his locked study and the operator must direct the detective to investigate, walking around the house in which the death occurred, examining things, and interviewing suspects. Aarseth comes to the conclusion that the operator, who is ignorant of the proper outcome and of what he or she is supposed to do, is actually not at all a “wreader” with strong authorial power, a similar conclusion to that which Buckles reached regarding Adventure. Instead, the operator is what Aarseth calls an “intriguee,” the target of an elaborate intrigue perpetrated by the designer of the narrative world. This is a kinder interpretation than, but similar to, one I made in “Interactor’s Nightmare,” an article on Suck.com that was published during the same month Cybertext came out. There, I suggested that the operator of an interactive fiction usually is in the same situation as the protagonist of Christopher Durang’s Actor’s Nightmare - thrust upon the stage without any warning, without having had time to learn lines or even know what play is being enacted. Aarseth’s concept of intrigue, discovered in his encounter with a work of interactive fiction, applies to other cybertextual experiences as well. It could be used to enlighten critical discussion of works such as John McDaid’s Uncle Buddy’s Funhouse and Rob Swigart’s Portal, which present puzzling worlds that the operator must decipher.
Aarseth only touches on the ludic nature of Deadline, though he at least makes mention of the game-like qualities of this and other cybertexts. In a comment on one specific Deadline interaction, Aarseth complains that some of the replies provided are “pure nonsense,” giving the example of the work’s response to the command “fingerprint me”: “Upon looking over and dusting the me you notice there are no good fingerprints to be found.” Actually the response, although unhelpful in the context of trying to win the game, is sensible, amusing, and perfectly apropos. Aarseth no doubt wanted his detective protagonist to perform an odd behavior: to stop, ink his hands, and record his own fingerprints on paper in the middle of an investigation. For the interactive fiction to parse his command differently and come up with an even more odd interpretation is not nonsense, but felicity.
In a 1984 Computer Games article, Dan Gutman urges operators to have fun by prodding the parser in similarly unusual ways: “after you’ve given up for the night trying to find out who the murderer is in Deadline or The Witness, have some fun with the computer. Tell it a joke. Insult it. Type in a sentence which makes no sense.” This sort of subversive interaction is not particularly uncommon in any sort of gaming or play situation, as children often use toys and software for purposes that are different from or even contrary to those intended by the creators of these products.
In interactive fiction, this subversive typing is an interesting way to interact, and has been recognized as such since early in the life of the form. Zork creators David Lebling, Marc Blank, and Tim Anderson mention this mode as one of two interesting ones (the other being the problem-solving mode of interaction) in their 1979 article in IEEE Computer: “a great deal of the enjoyment of such games is derived by probing their responses in a sort of informal Turing test: ‘I wonder what it will say if I do this?’ The players (and designers) delight in clever (or unexpected) responses to otherwise useless actions.” The operator using the text/machine in this way is engaged, and enjoys the text responses that are provided, but seems to be ignoring the overriding interactive and narrative purposes for which the interactive fiction was purportedly created. This mode, perhaps, offers the true “play” that these “games” provide. Solving puzzles in order to advance in the story is actually more work than play, related to mathematical and logical challenge more than ludic enjoyment. The operator who solves puzzles must labor to understand the author’s intentions and slog forward, learning the correct operation of the text machine and then operating it. The one who pokes at the interface to see what will happen is actually being playful.
In this chapter, as elsewhere, when Aarseth is not making strong original contributions, he is still practicing a basic standard of scholarship often not met by other writers. He corrects publication years given by previous authors; provides the names of actual interactive fiction authors, so often omitted in lieu of simply naming the publisher or pretending that the work sprang forth of its own accord; and insists that critics attend to other details with the same care they use in researching the citation of a printed text. That Aarseth attends so closely to the works he discusses is not a spectacular feature of the book, but such attention is necessary if previously neglected cybertexts are to be discussed alongside other works and treated with critical respect.
ghosts and the text/machine
The epigraph for Cybertext is from Italo Calvino’s provocative essay, “Cybernetics and Ghosts.” It reminds the reader that
The literature machine[‘s] poetic result will be the particular effect of one of these permutations on a man endowed with a consciousness and an unconscious, that is, an empirical and historical man. It will be the shock that occurs only if the writing machine is surrounded by the hidden ghosts of the individual and his society.
These ghosts are not a major topic of discussion in Cybertext. They flit outside of Aarseth’s text/machine triangle, without connecting to it directly as its verticies (operator, verbal sign, and medium) do. A moment of shock occurs during the encounter with any provocative text, whether generated cybertextually or not, and this moment is often profound and enigmatic. In the case of a cybertext, the shock can come not only from reading (the encounter with a particular permutation of verbal signs) but from reading in the specific context of text/machine operation.
It is this particular moment that may first have been experienced by Joseph Weizenbaum’s secretary, or perhaps one of the other early operators of Eliza, a computer character Weizenbaum developed to simulate a psychotherapist. Operators of Eliza type replies to questions in plain English. The text/machine then issues a noncommittal response, sometimes excerpting from what the operator has typed. Although Weizenbaum had been working on the program for several months in the presence of his secretary (as he relates in his 1976 book Computer Power and Reason), one day as she operated the text/machine, via a teletype, she asked him to leave the room so that she could converse in private.
A legend related by Janet Murray in talks after the release of her book Hamlet on the Holodeck offers a more powerful twist on this story. Entering his office one day, as the legend has it, Weizenbaum saw his secretary bowed before the teletype, broken down in tears. A transcript of interaction with Eliza was on the printout. “I’ve just had a breakthrough with my analyst,” the secretary explained.
Clearly, reading through a transcript of the same text, or clicking along links to read the doctor-patient dialog in a hypertext would not have had the same effect on this cybertextual operator. The operation of a cybertext such as Eliza is not only interesting because it results in a particular, provocative series of signifiers, but because it creates a context of operation - which might involve exploration, writing, and witnessing the reaction to what the operator has written, and engaging in other forms of advanced computational exchange.
Whatever the early cybertextual encounter of computer psychotherapist and secretary was like - tearful or not - in it, this shock of connection with individual and social ghosts was certainly achieved. And this shock occurred about 35 years ago, as Eliza was developed between 1964 and 1966. After this incident (and in part as a result of it, if legend is to be believed), Weizenbaum, a pioneer in artificial intelligence, denounced the field. He stopped his research and drowned his book.
Cybertexts long ago demonstrated their potential to be provocative, affecting, and powerful. Thanks to Aarseth’s book, a larger literary category has been declared worthy of critical attention - a category which includes Eliza, MUDs, poetry that involves text morphing and motion in response to input, interactive fiction, and other sorts of non-hypertextual works. Additionally, thanks to Cybertext, authors who create works in these forms are more likely to find their efforts acknowledged as valid from a literary standpoint. Critics may still prefer to examine hypertexts, if their tastes in text/machine operation lead them to dwell on that set of cybertexts, but they will find it increasingly difficult to consider other cybertexts - with their more powerful computational abilities and their demonstrated ability to affect the consciousness and unconsciousness of the operator - as categorically less serious and worthwhile.
Works Cited
Buckles, Mary Ann. Interactive Fiction: The Computer Storygame ‘Adventure’. PhD Dissertation, University of California San Diego, 1985.
Gutman, Dan. “Shoot Your Own Men! And Other Weird Ways to Play.” Computer Games. Dac/Jan 1984.
Landow, George. Hypertext: The Convergence of Contemporary Literary Theory and Technology. Johns Hopkins University Press, 1992.
Lebling, David P., Marc S. Blank, and Timothy A. Anderson. “Zork: A Computerized Fantasy Simulation Game.” IEEE Computer., 12:4, 1979: 51-59.
The original version of this text included interactive excerpts from the following programs:
Blank, Mark. Deadline. (Excerpt allowing play for the first hour of game-time.) Infocom, 1982. Excerpt created in 2000 by Nick Montfort using a port of Deadline to the Inform language. Port to Inform by Volker Lanz, 1999. Inform by Graham Nelson, 1993-1999. Excerpt created and used with permission of Activison, Inc.
Russotto, Matthew. ZPlet 1996. Java interpreter for Z-code, used to run the Deadline excerpt. Used with permission of Matthew Russotto.
Weizenbaum, Joseph. Eliza 1964-66. Java version created and made freely available by Charles Hayden, based on a 1983 Macintosh version by Charles Hayden.
Footnotes
-
Correction: According to Eskelinen himself, he said, ironically, “In the meantime please forget hypertext fiction. It stayed static and cybertext fiction replaced it.” ↩
Cite this review
Montfort, Nick. "Cybertext Killed the Hypertext Star" Electronic Book Review, 30 December 2000, https://electronicbookreview.com/publications/cybertext-killed-the-hypertext-star/