Ping Poetics

Sandy Baldwin investigates the manner in which a computer "ping trace" can be classified as a form of digital poetics, and discusses the underlying symbolic practices of both poesis and poetics that encompass coding and computation.
Sandy Baldwin investigates the manner in which a computer “ping trace” can be classified as a form of digital poetics, and discusses the underlying symbolic practices of both poesis and poetics that encompass coding and computation.⏴Marginnote gloss1⏴Baldwin’s essay on Digital Poetics was also recently published on ebr and can be viewed here: Against Digital Poetics.
Baldwin’s essay on Digital Poetics was also recently published on ebr and can be viewed here: Against Digital Poetics.
— Andrew Burchiel (Oct 2009) ↩
An earlier version of this essay was given at the 2008 Electronic Literature Conference in Vancouver, WA. Thanks to all who listened and commented.
“Only the imagination is real.” William Carlos Williams
Hello Baghdad. Hosts are open, packets receiving. I’m in Iraq in milliseconds. But the DoD turns me back, their firewall refusing to echo, ending my request.
I tell you the net is fields of waves and radiations. It takes us in and we take it in. It is netting, apparatus of capture. The net is defined as always on, connections always open. The earliest RFCs make fragmentation and addressing basic features of the net, not reliability. Questions of accounting and the economics of transfer - and this is the source of the term “logging on” - turn to problems of an interminable and intransitive writing. Once in the net, I can speak of datastreams and packets, of addresses and codes, of world travel.
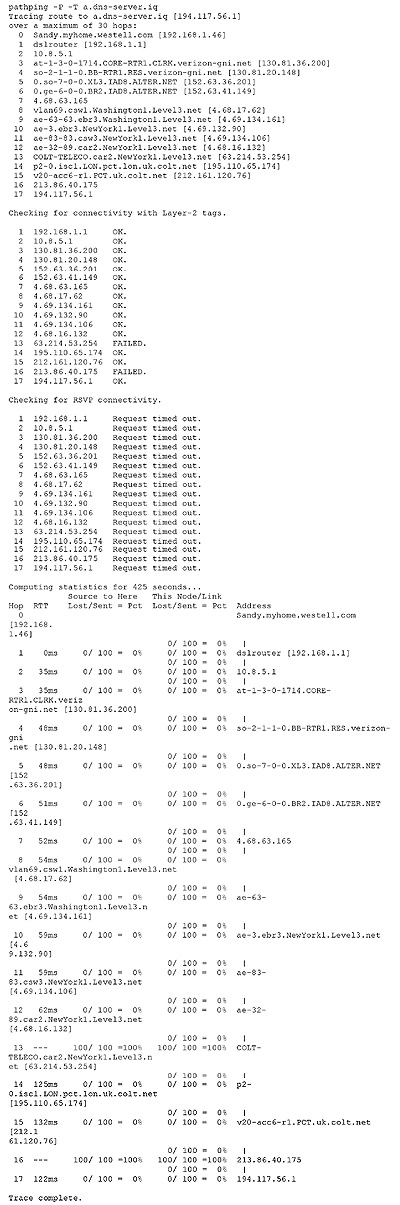
Here’s how I went to Iraq the other day. I rode the net and wrote into the net. Here’s what I did: I ran pathping in the command prompt that still remains below the surface of Windows, ran it from my home computer to a.dns-server.iq, the primary name server for the country of Iraq. The text included the word pathping, which is a command invoking a program of the same name, and included an internet address, which provided the destination for the pathping utility.
What is pathping? Briefly, it combines features of the older traceroute and ping network utilities. Versions of pathping or these other programs are built into most computer operating systems. The traceroute feature collects details of the path followed from my home computer to the address I supply on the command line, in this case a.dns-server.iq. Traceroute maps out nodes that are available on a system, showing paths, times of route, and so on. The utility pings network hosts along the way, requesting an “echo response” indicating that the host is available. Ping measures and reports problems of availability (machine available or not on the net), latency (time of transmission), and reliability. My computer sends out a datagram or a formatted “packet” of data consisting of nothing more than a request for response and “time to live” or TTL value. The latter is an upper limit on the number of host servers the packet can be routed through before reaching its destination. The TTL is designed to prevent the net from being clogged with endlessly circulating packets unable to reach destinations.
What was the outcome? A writing of my being on the net. See Figure 1: The result starts with my pathping command.
[Figure 1]
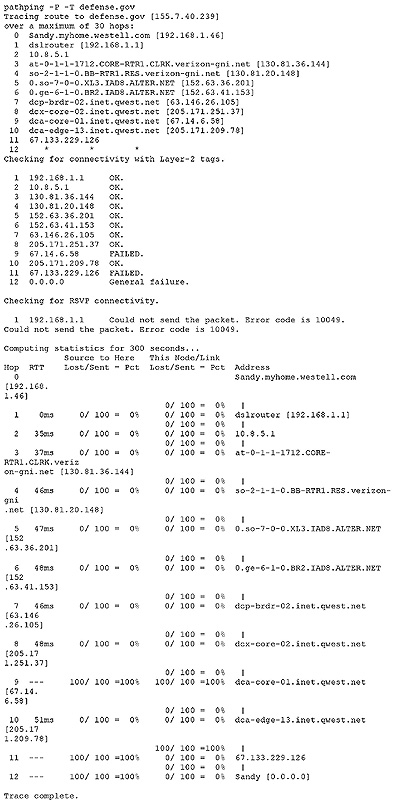
For comparison, see Figure 2, another pathping I ran from my home computer to defense.gov, the server for the US Department of Defense.⏴Marginnote gloss2⏴Test Gloss. Hello World!
— Dibs Roy (Nov 2013) ↩
[Figure 2]
What is written here? It took seventeen hops from my computer to the Iraq DNS Server and took twelve hops from my computer to the Department of Defense server, or at least until the pathping reached a point where the trace was blocked, presumably by the DoD firewall. I can see my route to Iraq passed through several hosts in the USA, including Washington DC and New York, then through several hosts in the UK, and finally to the Internet Protocol address 194.117 reserved for Iraq. I can also read the time taken for the ping echo message to return to my computer from the Iraq address. The result is a topographic measurement: 122 milliseconds from me to Iraq’s presence on the net. A topography of immediacy and presence through my machine.
What is the * or asterisk in the text? It is lack of response in answer to my request. My packet requesting a response reaches the DoD but I wait in vain. The time to live is exceeded and the packet dies and disappears from the net. The DoD ping is lost without an echo. My request for a response is never answered.⏴Marginnote gloss3⏴A zombie computer (often shortened as zombie) is a computer
attached to the Internet that has been compromised by a hacker, a
computer virus, or a trojan horse. Generally, a compromised machine is
only one of many in a botnet, and will be used to perform malicious
tasks of one sort or another under remote direction. Most owners of
zombie computers are unaware that their system is being used in this
way. Because the owner tends to be unaware, these computers are
metaphorically compared to zombies.
A zombie computer (often shortened as zombie) is a computer
attached to the Internet that has been compromised by a hacker, a
computer virus, or a trojan horse. Generally, a compromised machine is
only one of many in a botnet, and will be used to perform malicious
tasks of one sort or another under remote direction. Most owners of
zombie computers are unaware that their system is being used in this
way. Because the owner tends to be unaware, these computers are
metaphorically compared to zombies. For more information see: Zombie Computer Wiki.
— Andrew Burchiel (Oct 2009) ↩
There’s a masquerade to ping. Spammers send out pings to find new hosts, new sites to exploit. Is it not strange that the echo response, “yes I’m here, on the net,” is an invitation to infection, to invasion and incorporation into a zombie network. More and more websites refuse to ping. They filter out the response. Back at home, the sender gets asterisks indicating that the message ends there. Of course, this still maps the boundaries. I can still draw the lines of the net through the asterisks, but it is a withdrawn net, a topography of enclosures and fortresses, rather than responses. Or better, we would say that the net moves from one kind of response to another, indicating the basic relations and positions underlying response. The first is display of the site, an opening, the second a closing, a display of the surface and edge.
If you know enough, think of the Traceroute project started almost ten years ago through the trAce Online Writing Center by Alan Sondheim, Sue Thomas, and others, a project that traced a singular image of the net itself. It would be enough to see this project as the exemplary instance of the becoming-literary of the literal, of the nettings and knottings of the net (Sondheim 2000). This is the unary mark and limit I am targeting, caught in the constraints of the internet’s “physical layer.”
This writing is not - or hardly at all, ever so little - a text. This is both a philosophical and political statement. Philosophically, I say text is woven towards alterity, writing reading towards others. For there to be a text, there must be intersubjective structures of communication. Text requires response. Even if there is no sign of response, this lack is the signifier of the Other’s response. The other is written in and through text always in part and in whole my desire to the Other. Translate this into any discourse you want - that is, re-frame it in terms of institutions - and we can say that there is always a crowd in the text.
With our email and nicely served webpages - and these are the standardized image of digital writing - we are familiar with a net operating with TCP protocols that utilize gateways, localizations with enough global information to route individual messages and guarantee their delivery. Keep in mind that the network’s transmission and application layers are built to deliver. TCP, the Transmission Control Protocol, moves packets of information around the net in a single stream of data and commands. TCP is, after all, a reliable protocol, guaranteeing correct delivery, and yet is built via fuzzy logic on the unreliable net. TCP assumes communication, “association between two or more entities without regard to path,” in the words of the original protocol document, assumes communication as association, that is, assumes the net as alterity, as the presence of others, as the multitude. The crucial point is that the TCP stream maintains the priority of delivery, queuing up data packets in the receiving node’s buffer, and guaranteeing that messages arrive with the right parts and in the right order. TCP is writing that implies a textual model of reading order and hierarchy, of packet segmentation as annotation, and packet length and format as closure of the book. The writing of TCP is a contractual relation. The segments and packets, addresses and check digits, are dedicated and written towards the other. TCP creates virtual circuits between nodes that are listening and ready for association. It is a philosophy of alterity, where “I write” means “I listen for the other, I wait for your reply.” More than this, TCP assumes that the other will listen and reply. The protocol’s reliability is because you and I already enter into this listening relationship, in every TCP-driven communication, whether email or html page. My existence online is a contractual relation to listen for you. Such a contract is writing that situates and precipitates the other and myself in the presence of the network. This last is important to the crowd: the network is silent witness to our bond. As a crowd we are segmented, written with the network. We are in our place, receiving the signs on screen. TCP assumes communication, “association between two or more entities without regard to path,” communication as association, that is, assumes the net as alterity, as the presence of others, as the multitude.
By contrast, traceroute and ping work with the IP or Internet Protocol, a connection-less best-effort datagram service, with no guarantee of end-to-end reliability. IP and TCP co-exist, but TCP can be said to ride on IP in the hierarchy of internet layers. The IP domain of net packets remains a pack without direction and place, only committed to increase and flow. The relation is unstable, a “leaky abstraction” in the words of Joel Spolsky (Spolsky 2002). Texts written and received against a field of messiness and flux, writing as gesture and display. As defined by Braden, “IP datagrams may arrive at the destination host damaged, duplicated, out of order, or not at all” (Braden 1989). IP allows the undefined, the infinite, the failed, and the wild. TCP attempts to describe and formalize the underlying spew, to treat it as reliable, to leave a mark in the place of the leakiness of abstraction. The result is any number of problems of formalization many of which are exploitable by hackers through phishing, spoofing, and Denial of Service attacks. For example, a “ping flood” is a simple DNS attack, clogging bandwidth, while the “Ping of Death” exploits the upper limit to the size of a message or text. A host is tricked into re-assembling a message larger than the maximum IP packet size (65,535 bytes), even if it is larger by one byte, leading to a buffer overflow and a crash. Note here a basic poetic problem of length and form of the text, we might say of the form of the book beyond the book in the sense of Edmund Jabes or Maurice Blanchot, here challenged by a kind of production that enters into the form and destroys it, with comparison to a range of innovative poetics.
Ping is a drifting term for net communication. The blogosphere resemanticzed ping as a message pushed to servers from a blog announcing the blog is updated, leading to new forms of ping spam or sping. Artworks explore ping. In Pawel Janicki’s “Ping Melody,” performers improvise on voice and cello in response to mappings of internet pings (Janicki). Janiki claims the performance produces reflection on the techno-military structures of the internet. The imaginary projection in Janicki’s aesthetic is the promise of the becoming-readable and discursivity of ping in the improvised performance. In Stelarc’s “ping body,” audiences could “remotely access, view and actuate [the artist’s] body via a computer-interfaced muscle-stimulation system based at the main performance site” and cause random movements according to the space-time of pinging. The body moved in the “physical and collective space of the net” (Stelarc 1996).
When I say this is not - or hardly at all, ever so little - a text, when I say this is also a political statement, I am insisting on the stakes of the discourses we enter into, of the stakes involved were I to say (for example) that this writing is electronic literature. Of course we read narrative in this (k)not text. Look at my pathping: isn’t it a compelling story? A high adventure? Engagement in Iraq and encounter with national security. I think of the late J. G. Ballard’s disaster narratives or cracking the ice of the Eastern Seaboard Fission Authority. Suspense, international travel, geopolitical drama, ripped from the national news. I tell you this is a narrative. I can just make it out through the codes here. Even more, the codes add to it, suggest the insistence of the real behind the narrative. Isn’t this insistence the case? Is this not a mapping of net, and with this a kind of mapping of the world? Is this not a story to read about global relations? The traces in the writing - the names of cities and locales, and my name - are a meta-code bringing this text into significance, locating the world in terms of my story. For instance, what’s going on with those Iraqi servers, wonderfully named .iq? We could talk of the whole corrupt drama of marketing and capitalizing on reselling Iraqi nameservers.
This is a kind of theoretical knowledge, a discourse built on the response recognized in the pathping writing. Such a story recognizes the desire of the other at work in this writing. These are problems of boundaries, of constituting the subject of the net and the subject’s knowledge of the net, of the internet protocol suite as the ontology of being online, and of what I give or donate to the net, rather than discursive problem of what we say of the net. I say that the flux and tolerance of maintaining the net is more important than the nodes and gates of communication. My ping is still out there, circulating in and out of the DoD net, whether the host responds or not. Packets move from host to host, in the same way. The net is indifferent; the ping is just another packet in the flow. The difference is the semantics of response and reading. In terms of IP, “destination unreachable” means “distance to the network is infinity.”
The (k)not written into the net does not signify. Before the text is text I must already constitute the network, I must introject the net and the perception and knowledge of my being online as the condition of reading this text. I imagine the net. It is my fantasy. To read this writing as a text, towards all the others that compose it, to constitute me as a node in the net. The discovery that the text is the product of continual logging and processing in my computer means I read towards an anonymous other, a structural other that I posit or project across the space of the net.
I’m becoming hysterical. I’m hystericizing this discourse to you, I’m turning provocative.
I say that there is no - or hardly any, ever so little - electronic literature; that in any event there is no essence of electronic literature, no truth of electronic literature, no electronic-literary-being or being-literary of electronic literature. This is both a philosophical and political statement.
Philosophically, there is a literary critical discourse on electronic literature that pragmatically deals with the part objects and projects of writers. To take a single theoretical claim as proof, consider the “flickering signifiers” described by Katherine Hayles (Hayles 1999, 30). I take these for the unquestionable importance of Hayles’ work, which underlies so much of the literary critical discourse on electronic literature, and for the specific importance of flickering signifiers in her work, as the model for her later conceptual tools such as the technotext and “media metaphors.” You recall, of course, that she takes off from Jacques Lacan’s notion of a floating signifier, but sees Lacan’s notion as far too print-based. By contrast, she argues that “flickering signification is the progeny of the fascinating and troubling coupling of language and machine,” and that the flicker is the proper phenomena in the posthuman era of digital patterns.
The basic literary critical notion is of being able to read off signifiers as surfaces juxtaposed to an apparatus, or “material instantiation” in Hayles’ favored terminology, and to make the functioning of this juxtaposition a revelation of the subject and culture around and through the apparatus. As with all rhetorical technique, the method is persuasive and the interpretive dividend reliable. It is not surprising that Lacan’s discussion of floating signification comes in the context of the rhetorical exemplification of the signifier in tropes and figures, nor that Hayles’ discussion of flickering signifiers concludes through a series of readings of literary texts mapped onto the transposed rhetorical schematic of the Gremaisian semiotic square, and not at all surprising that all this assumes the functioning of language as a cultural medium, as a semiotic apparatus, a conclusion rather far from Lacan’s position - rather than the position he describes and critiques - that is, the position that the signifier does not exist, even that language does not exist, only as a body and as the symptomatology of bodies.”What has a body and does not exist? Answer - the big Other,” said Lacan (Lacan 2007, 66).
As befits the inheritance of rhetorical tradition in literary criticism, the literary critical discourse on electronic literature calls upon and uses, I would say uses up and consumes, literature to exemplify the functioning of institutions. Nothing more and nothing less is the point of rhetoric. The literary critical discourse on electronic literature provides institutional accountings of value: the value of texts, their circulation, the identity of their authors, the need for their preservation, and so on. Of course, Hayles’ signifiers “flicker,” just as Lacan’s signifiers “float” because both deal with signification as a network in relation to the other. The sign is written and read in relation to the big Other, and this means to culture and institutions. I can’t fully connect the dots here, but let me say this is the same “leaky abstraction” I wrote of earlier.
When I say that there is no - or hardly any, ever so little - electronic literature, when I say this is also a political statement, I say that for myself I forego the literary critical discourse on electronic literature. I leave it to you - you can have it. I see no need to recapitulate the positions and history of literary criticism on writing in electronic media. No doubt, rebranding such as the turn to Web 2 or Critical Code Studies provide added descriptive precision to the discourse.
I am not making the banal point of questioning the value of these approaches, nor the value of what I call the literary critical discourse on electronic literature. Rather, I say our question should be, instead of the existence or essence or thing of electronic literature, I say we should ask: What is electronic literature after? By this I mean at least two things.
Firstly, what does it desire? What do we want with the institutions we build, the works we collect, the essays we write. At the least, if what we want is more of the same, then we can name the capitalizations involved. Beyond this, we need intense focus on the subject and work of writing the net to name the surplus pleasure, the other satisfaction of this pursuit. Again, boundary issues, the liminal and fuzzy spaces of the territory and the wild, net and machine sites of poetic production and becoming-literary. And so, “what is electronic literature after” also means what is it following, what track and what event does it pursue? The (k)not of pathping writing is one thing.
Works Cited
Braden, R.. “Requirements for Internet Hosts - Communications Layers (RFC 1122).” Internet Engineering Task Force Tools. Accessed January 22, 2008.
Hayles, N. Katherine. How We Became Posthuman. University of Chicago Press, 1999.
Lacan, Jacques. The Other Side of Psychoanalysis. W. W. Norton & Co., 2007.
Janicki, Pawel. “Ping Melody.” Pawel Janicki. Accessed April 8, 2008.
Sondheim, Alan. “The Traceroute Project.” trAce Online Writing Center. Accessed April 8, 2008.
Spolsky, Joal. “The Law of Leaky Abstractions.” Joel on Software. Accessed April 8, 2008.
Stelarc. “Ping Body.” Stelarc. Accessed April 8, 2008.
Cite this essay
Baldwin, Sandy. "Ping Poetics" Electronic Book Review, 2 October 2009, https://electronicbookreview.com/publications/ping-poetics/