Sublime Latency and Viral Premediation
In Sublime Latency and Viral Premediation, Kim Knight addresses the “eco-poetics of the viral” across the biological, social, and digital. Through an analysis of the spread of digital infection, the dynamics of anti-virus software, and digital arts practices, Knight discusses a poetics of fear and desire that is instrumental to the transmission of this virtual pathology. Knight continues, drawing parallels with crowdsourced epidemiology apps that track illness and promote physical health, and makes a powerful case for what Richard Grusin has called the “premediation” of anxiety as a strategy for managing affect in the 21st Century.
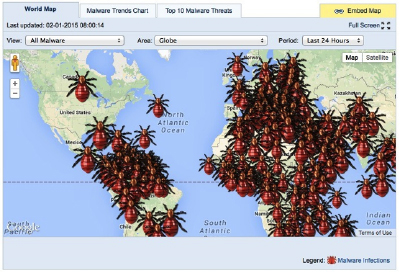
Fig. 1 Screenshot of the ESG MalwareTracker Worldwide Infection Map
One glance at the ESG MalwareTracker (fig. 1) is enough to make one’s skin crawl. Borrowing a visual strategy from epidemiology, MalwareTracker uses a map to depict computer virus infections worldwide. The map is dotted with red insects with shiny bulbous bodies that appear to be sized in proportion to the number of infections in a location. There are only three discernible sizes, representing 11 suspected infections at the low end (Cape Verde), up to 1.7 million at the high end (the United States). Each country has just one insect to represent the number of infections. The effect is that areas of the world with very large territories, such as North America, look relatively empty, while South America, Europe, Africa, and the Middle East seem positively infested.
Although the epidemiological is often one of the ways in which digital contagion is framed, the use of the disease map is fairly novel. The fallacy of the map, which privileges location, is that computer infections do not require shared geography. If we push harder against the bio-computational join, however, the map might prompt us to think about ways in which biological disease also belies shared geography. We might think about the ways that global travel patterns and the movements of animals complicate the representation of person-to-person transmission of the biological virus. Despite the limited utility of this map for tracking and avoiding infection, the map still functions as a representational object that exemplifies anxieties about contagion. It is also indicative of the feedback loops that operate between different contextual iterations of the viral.
In this essay I examine the operations of the viral across and between contexts as it deterritorializes and reterritorializes between the digital and the biological in order to elucidate an eco-poetics of the viral. I begin with the work of defining the viral and connect its characteristics to Burke’s sublime to establish its anxiety-inducing effects. I then evaluate how sublime latency manifests in Sneha Solanki’s art installation The Lovers, including a reading of the anthropomorphized computers and underlying romantic hacker mythos that trouble biological-digital distinctions and expose the vulnerability of the human operating system. I then examine antivirus software as a response to anxieties regarding the sublime latency of the viral and suggest that it deploys a logic of premediation that shapes user behavior and extends its own sociotechnical network into the future. Finally, I turn to social illness forecasting software to examine how the logics of the digital are reterritorialized into the biological in the service of capital and securitization.
The word “virus” is defined according to its biological, digital, and social uses. Through these different contexts, each definition retains at its core the concept of infectiousness, which is generally achieved by being submicroscopic or unforeseen, circulating despite control structures, and being self-replicating. These concepts, “submicroscopic,” “unauthorized,” and “self-replicating” describe the production and transmission of the viral structure as it moves across media ecologies. The viral structure includes the viral object as well as the discourse communities and technological platforms that facilitate transmission. The viral structure is mobilized by subjects who are “unauthorized” to produce or circulate information, or in direct challenge to powerful institutions or established practices. The viral structure may reproduce through acts of mechanic or algorithmic replication, or it may be considered “self-replicating” in the sense that the users who share the viral structure could be considered part of its reproductive system. When a viral structure self-replicates, its users are engaging in unconventional reproduction via acts of replication, iteration, or discussion. In other words, self-replication of the viral structure can be considered one of the modes of participatory culture. Not all participatory media are viral structures, but all viral structures are participatory. In addition, the effects of the viral structure as self-replicating have the potential to feed into and reinforce its unauthorized operations.
In considering the characteristic “submicroscopic,” it is helpful to theorize the various ways in which something might refuse or complicate visibility. In some cases, this means that the viral structure complicates traditional notions of media hyper-visibility. Without the amplification that comes from the resources of mainstream PR and marketing structures, viral media objects often circulate outside of mainstream media channels, with a sort of functional invisibility. In other cases, such as computer viruses or biological viruses, the viral structure is actually undetectable to or obscured from the human eye and only visible through its embodied or computational effects. Generally, it is not until a person begins exhibiting symptoms or a computer begins to behave erratically that the viral structure becomes intelligible, though the virus itself likely remains invisible.
The invisibility of the computational or biological virus creates a particular affective response. In A Philosophical Enquiry into the Origin of Our Ideas of the Sublime and Beautiful, Edmund Burke1 writes, “to make anything very terrible, obscurity seems in general to be necessary” (54). The invisibility of the virus couples with its nature as unauthorized to result in an experience of the sublime. What cannot be seen cannot be contained. What cannot be detected can replicate with abandon. And that which self-replicates without constraint threatens the integrity of the host, whether it be computational or biological. Thus the sublime effect of the virus is also due to the quality of infinity, which Burke suggests can be experienced either in terms of vastness or extreme minuteness (66-7). In the case of biological viral structures the infinity is the infinite minuteness of the microbe. Burke writes,
when we attend to the infinite divisibility of matter, when we pursue animal life into these excessively small, and yet organized beings, that escape the nicest inquisition of the sense; when we push our discoveries yet downward, and consider those creatures so many degrees yet smaller, and the still diminishing scale of existence, in tracing which the imagination is lost as well as the sense; we become amazed and confounded at the wonders of minuteness; nor can we distinguish in its effect this extreme of littleness from the vast itself (66).
In terms of the computer virus, the computer, its algorithms, and the vast network act as a black box in which the edges of the field cannot be discerned. Burke writes, “But the eye not being able to perceive the bounds of many things, they seem to be infinite, and they produce the same effects as if they were really so” (67). The black box effect adds an additional layer of opacity onto the infinite minuteness of bits. We might describe the viral as having a sublime latency, which is shorthand both for how it behaves and for the affective response it causes.
According to Burke, the literary arts are the most sublime, and of those, poetry has the most power to obscure (57). Poetry is the carrier of the virus in Sneha Solanki’s art installation, The Lovers. The Lovers was part of a 2003 Transmediale exhibit entitled, “I love you computer_viruses_hacker_culture,” that featured art inspired by the “I Love You Virus” that plagued computer users in 2000. The “I Love You” viral structure was spread via an email with the subject line “I Love You.” The virus was contained within a file called “LOVE-LETTER-FOR-YOU.TXT.vbs” and is recognized as being an early example of email-based social engineering (Seltzer). The exhibit was composed of a variety of artworks that took the virus as inspiration. The Lovers consists simply of two computers, networked with only one another. The white computers sit on tall white rectangular pedestals, tethered together by a network cable. The uniformity of color and the proportions of the monitors and pedestals give an anthropomorphic impression in which the monitors appear as heads and the pedestals as bodies (fig. 2).

Fig. 2 The Lovers at Watson Institute, Providence USA. 2004. Image source: electronicartist.net
When viewed through such a lens, the network cable appears to connect the two machines right at the heart. Each computer terminal displays the text of a love poem written by a Romantic poet, a tradition that often focused on the sublime. On one is “A Red, Red Rose” by Robert Burns, a poem about the beauty and thrall of new love. On the other is “Where, oh ! where, on his restless wing” by Eliza Acton, which also relays the thrill of new love but tempers it with wariness regarding the after-effects of that thrill. At the beginning of the installation, one of the computers is infected with a virus. It is most likely on the Burns machine since the last two lines of the Acton poem read, “Though rapture dwell in thy sunny smile / Despair comes fast on thy steps the while!” Burns’ speaker is all in rapture while the second speaker in Acton’s poem addresses Love personified and asks “But ne’er again in thy roamings come / To make my bosom thy passing home.” Having been betrayed, she is willing to forsake “wild intensity” to avoid the despair that is likely to follow. In the selection of these two poems, displayed in an arrangement of anthropomorphized hardware, networked together in such a way that the rest of the world disappears, Solanki has already imbued the installation with a level of affect. There are affective relations between the computers, but also between the viewer and the computers.
Solanki’s choice of virus amplifies both the sublime and the romantic. Her website lists “VIRS0245.COM” as one of the project’s three files (the other two being the text of the poems).2 Information on VIRS0245 is sparse and contradictory. In one account, VIRS0245 is a variant of the “Stupid Virus” that corrupts and overlays files (Martin). In another, it is a Trojan horse that a hacker hid inside a file distributed by PC Magazine and that wrote bad sectors onto a hard drive (Sunet.se). In the most interesting account, the virus is labeled a “harmless memory resident” (Computer Incident Advisory Capability). Despite labeling the virus as harmless, this account is intriguing both for its description of the virus and for its attribution to the hacker behind the virus. The CIAC page points the reader toward the December 1992 issue of Virus Bulletin, where the reader finds analysis of “Commander Bomber,” one of VIRS0245’s aliases. The writer at Virus Bulletin notes that “Commander Bomber” was initially thought to be so dangerous that antivirus vendors did not release information about it, claiming fear of inspiring copycats (Anonymous 10). However, both CIAC and Virus Bulletin assert that the virus does little damage. Part of the “danger” noted in Virus Bulletin is that despite the fact that the virus is not encrypted, it eludes typical tracing methods. “Commander Bomber” is the first virus that inserts its code into random places in a file, thereby obscuring its presence to contemporaneous virus scanning software that only scans the beginning or end of files under inspection (Anonymous 10). “Commander Bomber” increases the obscurity of the virus, repudiating attempts to detect its presence through antivirus software. It refuses the “nicest inquisition of the sense” (Burke 66), thereby ensuring its own infectiousness and the sublime experience of encounter. This virus is particularly sub-microscopic.
Solanki’s choice of this virus for The Lovers is interesting for another reason. The CIAC page attributes authorship to a Bulgarian hacker named Dark Avenger. In reference to the attributed authorship, the Virus Bulletin analysis states, “my own feeling is that this code is beyond [Dark Avenger’s] limited capabilities” (10). However the Virus Bulletin writer acknowledges the source of the virus as originating in Bulgaria and offers no alternative theory of authorship. Numerous other websites credit Dark Avenger with creating “Commander Bomber,” resulting in a pervasive cultural narrative that zhe is the author.3 The mythology around Dark Avenger has a dark romanticism that complements the affective qualities of Solanki’s installation. David Bennahum describes a sort of virtual courtship between Dark Avenger and Sarah Gordon, a psychologist and security professional who became interested in viruses after purchasing an infected PC in the early 1990s. Gordon began visiting FidoNet, where Dark Avenger caught her attention. In an attempt to attract zher attention, Gordon professed that she would like to have a virus named after her. Dark Avenger obliged. In a virus called “Dedicated,” zhe included the line, “we dedicate this little virus to Sara [sic] Gordon, who wanted to have a virus named after her.”
According to Bennahum, Gordon was the only person to ever meaningfully connect with Dark Avenger. Zhe allowed Gordon to publish an “interview” that is a collage of their email exchanges over a five year period. As with any good gothic hero, Dark Avenger has a foil, Vesselin Bontchev, whom Gordon repeatedly asks about in the “interview.” Her inquiries are rebuffed with petulant responses that include theatric gems such as “the weasel can go to hell” (Gordon). In a dramatic move, Dark Avenger reportedly dropped all contact with Gordon after zhe learned Gordon was getting married (Bennahum). In her interview, Gordon notes that many think that Dark Avenger and Bontchev might be one and the same (Gordon denies it). There has also been speculation that Gordon herself is Dark Avenger (see e.g. Kohntark). For those familiar with the dark and romantic mythos surrounding Dark Avenger, the use of VIRS0245 will amplify the sublime and gothic effects of Solanki’s anthropomorphized computers exchanging Romantic poetry.
During the installation, the two computers display their love poems and through a repeated exchange of the virus, the operating systems of both machines eventually break down. Solanki’s description of the process on her website deepens the anthropomorphism of the two machines:
A breakdown in the relationship was inevitable once the virus had seeped into the memory of one machine and then into the other through a singular network cable affecting the poetic text files. Communication between the two deteriorated, leading to irrational & at times odd behavior. Each machine reacted with equal confusion and conflict. The interface text became an illegible poetic mutation of itself.
Solanki’s use of “singular” to describe the network cable may be read as “only,” but we may also read it as exceptional, as in the extraordinary connection between these two lovers that ultimately leads to their demise. Communication deteriorates like that between a couple headed for a breakup. The computers behave irrationally, confused and in conflict, like lovers caught in the heat of an argument. The interface text mutates and becomes illegible, like the illegibility of vows, the mutation of utterances of endearment and declarations of love as a relationship disintegrates.
Although we know this is the work of the code in VIRS0245, we might speculate that these machines, in their anthropomorphic form, are in a way also infected with the passions from the poems. Burke describes the sublime power of poetry as having the effect of transmission: “by the contagion of our passions, we catch a fire already kindled in another, which probably might never have been struck out by the object described (159). Thus we may read the machines as infected by a virus that draws together the love poems, the malicious code, and the tumultuous melodrama of Dark Avenger and Sarah Gordon. As part of the viral structure of the ILoveYou virus, Solanki’s art piece reterritorializes the virus by imbricating the algorithmic with the affective and passionate. The humanity of the anthropomorphized computers engaged in the disintegration of communication and the breakdown of the relationship emphasizes the role of the human and invites us to contemplate the wild success of ILoveYou’s unauthorized self-replication as a biological problem in addition to a computational problem. It draws our focus to the fragility of the human operating system, easily exploited by social engineering and easily compromised by the passions. The Lovers makes no attempt to inoculate against infection, whether it be via code or passion, and the viewer can only bear witness to the ensuing breakdown.
Outside of the realm of art, the anxiety induced by the sublime latency of the viral is forestalled through a logic of premediation. In Premediation: Affect and Mediality after 9/11, Richard Grusin traces the intensification of premediation in the service of a post 9/11 regime of securitization. Practices of premediation arise from the desire to avoid the kind of cultural shock experienced in response to 9/11 by premediating multiple virtual futures, which maintains a constant low level of anxiety (2). Though Grusin focuses mainly on the increase in premediation after 9/11, he notes that the logic of premediation pre-dates September 2001.
Antivirus software, the market for which arises out of the sublime latency of the digital virus, is an integral part of the viral structure of ILoveYou and other digital viruses as an ongoing, automated process of premediation. Antivirus software is big business, with industries grown up around the software itself, as well as independent testing agencies, and even crypting services used by Hackers to test malware against large batches of antivirus software. After the release of the most recent Microsoft Security Intelligence Report there were numerous blogs posts and news stories focused on the number of unprotected computers worldwide. The media, engaging in the logic of premediation, necessarily focused on the report that 25.2% of computers are unprotected. An interpretation not committed to premediation might instead focus on the 74.8% of PCs worldwide that are protected by real-time antivirus software (Batchelder et al. 90).
However, this is not how premeditation functions. Grusin describes the functions of premediation in three different ways. Two of his ways of framing the concept apply to antivirus software: as “the remediation of future events and affective states,” and as “the extension of sociotechnical media networks into the future” (6). The software, through its process of continually updating signatures or definitions, premediates multiple possible connected futures in which the human-computer affective feedback loop will be under attack from forms of malware. In addition, the logic of the software extends the technocultural network of virus-hacker-infected-antivirus into the future. This future is an indefinite repeating sequence of antivirus professionals speculating on future forms of malware and virus authors developing new modes of obscurity to elude antivirus software.
Part of this cat and mouse game of premediation is found in the antivirus software signature / definitions update. Viruses are generally not visible to users, but “the inquisition of the sense” (Burke 66) of antivirus software finds them by looking for indexical signifiers of a virus’ presence: detecting code snippets or behavioral patterns of already known viruses. The antivirus software has to be updated quite frequently in order to keep up-to-date with new developments in code or behavior. In the course of regular computer use, unprompted by the user, the software sends a signal via an on-screen notice. This may be a reminder for the user to update the software, or more commonly in recent software, a notification that the files have automatically been updated. The update is a gesture of anticipation, both the anticipation of new connections and the anticipation of infection. This anticipatory gesture is part of the affective feedback loop that Grusin locates between user and machine (105) in which the notice anticipates and enables the possibility of further browsing and infection. In the pop-up message, the machine demands notice from the user; it acts as an unbidden, ghostly premediation of the sublime threat of the latent virus.
This is not a prediction or a reminder. In fact, Batchelder et al. found that despite the number of ever-increasing malware attacks, only 21.5% of Microsoft’s antivirus software users encountered malware during the period July 2013 - June 2014 and fewer than 1% of computers were infected (56). The encounter (and presumably the infection) rate is even lower in the U.S. with just 12.3% encountering malware in the second quarter of 2014 (Batchelder et al. 65). Despite the low level of infection, the ghostly signal of the update engages in a process of premediation that maintains a constant low level of fear. If, as Grusin notes, the premediation of fear with regard to terrorist attack is maintained through its embedding in the everyday repetition of televisual media, then surely the antivirus update signal, embedded on a regular basis in everyday practices of computing, is also “generating and maintaining a low level of anxiety as a kind of affective prophylactic” (Grusin 46).
The rhetoric of the Enigma Software website (publishers of MalwareTracker) parallels the rhetoric around individual freedom and threat that is used by the media in premediating terrorist threats: “The Internet is the first mass medium in history in which ultimate power resides in the individual computer user, and it was built on the concepts of transparency, choice, and user control. However, the individual’s power is only as strong as the software tools he or she uses, and it can be eroded by practices that hide a program’s actions from the user or that fail to function as expected” (sec. Mission Statement). This is another form of social engineering. Where ILoveYou drew on the vulnerability of human emotion, Enigma attempts to operationalize the fear of hidden viruses and human error. An uninfected machine is positioned as synonymous with the power of the user, which can only be maintained by the might of one’s software. Thus Enigma both premediates a virtual future and suggests the solution to safeguard against it. The software included in Enigma’s “Total PC Security” package reinforces the parallels with the rhetoric of national security with names of products that could be straight out of a Tom Clancy novel: SpyHunter, RegHunter, and SystemMedic are the team of algorithmic operatives protecting the sanctity of the individual, pre-empting the kind of breakdown that we see in The Lovers. We have moved from romantic poetry to an espionage thriller.
These agents go to work through the functions of monitoring and scanning, another way in which antivirus software performs premediation through anticipation. In these functions, the data from updates is used to monitor software behaviors and scan the source code of files. These scans may occur as users open individual files or during periodic total system scans. If malicious code is detected, the system sends another ghostly signal, in the form of a pop-up notice, that it has found an infection. These signals tend to include signifiers of heightened alarm, through the heavy use of the color red, alarm symbols, and exclamation points. However, the alarm in these cases is generally directed at the anticipated future of what could have been. The invisible and unauthorized virus has been detected and stopped, by deleting the file or placing it in “quarantine.” The notice of infection is both embedded in the present moment in which possible damage is thwarted, but also a premediation of possible viral futures. It may even be an indicator of an obscured viral present.
The sublime latency of the viral cannot be escaped, even when antivirus software is on the job. The invisibility of the virus means that it is entirely possible that a machine protected by antivirus software may be infected without the user’s or the av-software’s knowledge. For instance, the myth that Macintosh computers do not get viruses is often countered by the suggestion that many Macs are in fact infected with viruses that could harm a PC were they to be connected. Stuxnet and Regin are high profile instances of malware that went undetected for many years (estimates are two and six years, respectively). The targets of these viruses were high stakes persons- and organizations- of-interest in state espionage and warfare. However, average users may also be encountering undetectable viruses intended for their operating system. Much of the malicious code circulating on a daily basis goes undetected by antivirus software. In tests run over the course of a year by LastLine labs, researchers found that on the first day of testing, only 51% of the antivirus products being tested were able to detect the malware that they had introduced. It took two weeks for there to be any significant improvement, which still only rose to 61%. After a year, 10% of the software being tested had not detected all of the virus samples that LastLine had introduced (Vigna). Thus the scan notice is not only a notice that infection has been found and blocked, which has the effect of making the virus intelligible to human sense; it is also a gesture of anticipation that suggests that a multitude of viral futures is possible and that there may be malware currently lurking on the system undetected. False positives, misidentified infected files that some security professionals attribute to “more aggressive” detection (Lambert par. 5), also perform anticipation and form part of the affective feedback loop between user and machine. Even when no infection is found, the “all clear” notice subtly performs the anticipation of virtual viral futures. This is the textbook case of premediation: in the pronouncement of the integrity of the system, the software simultaneously premediates a future in which the user may not be as fortunate, thereby remediating future affective states and extending the sociotechnical network of user-hacker-software into the future (Grusin 6).
In mid-2014, Brian Dye, an executive at Symantec, the makers of Norton Antivirus, famously declared antivirus dead (Newman). Dye was not, of course, suggesting that users were no longer under the threat of infection from a digital virus. In fact, last year Kaspersky Labs reports that they detected over 123 million malicious objects (Kaspersky 11). Dye, however, cited Norton’s catch rate of only 45%, and suggested that the approach to information security must shift (Newman). The latent sublime is such that antivirus software and virus definitions hosted on individual endpoint computers are no longer sufficient. Symantec is formulating “a new approach that focuses on spotting hackers within a system and minimizing damage from them instead of trying to keep them out” (Hay). Indeed, few of even consumer grade security products rely exclusively on antivirus detection. Many products now offers security suites that combine antivirus software with software that repairs infected files, monitors browsing, detects spyware, and filters spam. This combines with firewalls built into modems and other security measures that layer anticipatory moves onto those performed by antivirus updating and scanning. Dye’s splashy declaration of the death of antivirus software does not signal that antivirus is going away any time soon, but it is a unique act of premediation. The assertion that infection is inevitable and that the landscape of online threats is much larger than can be handled by antivirus software shores up the logic of premediation under which the user maintains a constant low level of anxiety. It additionally frames the security marketplace as one in which the user who “merely” has antivirus software is courting danger.
One of the most salient qualities that sets premediation apart from prediction is the effect that it has on the present (Grusin 8). The virtuality of possible futures is remediated into the actions and effects of the present. In 2005, the Pew Internet and American Life Project conducted research on whether the threat of malicious software affected how people use the Internet. They found that nine out of ten computer users adjusted their online habits, with 48% no longer visiting websites they would have otherwise and 25% no longer using peer-to-peer networks for downloading (Fox 2). The attitude that certain users invite infection through their habits emerged contemporaneously with malware itself, in which the computer user was reminded of their individual responsibility and blamed when he did not practice “safe hex” (Parikka 127). In Sarah Gordon’s article, “Inside the Mind of Dark Avenger,” she chides Dark Avenger for the effect that his software has on innocent users. He responds, “The innocent users would be much less affected if they bought all the software they used (and from an authorised dealer) and if they used it in the way they are allowed to by the license agreement. If somebody instead of working plays pirated computer games all day long, then it’s quite likely that at some point they will get a virus. Besides, there’s no such thing as an innocent user, but that’s another subject” (Gordon). The user with bad habits is deserving of infection, both for the act of piracy and for engaging in unauthorized play instead of proper work. Even those who created and disseminated viruses believed that users can and should protect themselves by using their computers and the Internet only in authorized ways.
In June 2014, shortly after Brian Dye declared antivirus dead, CNet’s Rick Broida published an article titled, “I Don’t Use AntiVirus Software. Am I Nuts?” Though the title of this suggests a carefree approach to computing on Broida”s part, the reality is that he has many safeguards in place to protect his computer. He describes using a secure operating system, which he keeps meticulously up to date. In addition, his modem has a firewall and he uses browsers that have security measures to prevent accidental browsing to malicious URLs. He uses the browser plugin “Web of Trust” to vet sites before visiting and is cautious about clicking links and downloading files. This is all supplemented with an occasional scan using Malwarebytes, a free tool to detect and remove malware. So while Broida may have freed himself from the financial shackles of purchasing antivirus software, the logic of viral premeditation still operates in that the affective anticipation of infection governs his computer usage. This kind of “safe” usage places constraints on the flow of Broida’s browsing and shapes the contours of his identity as it is distributed across multiple sites.
Unconstrained connectivity and distributed identity are the cornerstones of new forms of immediacy and hypermediacy that characterize the age of premediation (Grusin 2). Immediacy and hypermediacy are impacted by the latent sublime of the virus and the logic of viral premediation, which shift computing habits towards the more conservative. By conservative I refer to habits such as those described by Broida, but also the prevalence of social media sites in American computer usage. 71% of American internet users use Facebook and 52% use multiple social media sites. Of Facebook users, 45% visit the site several times per day (Duggan et al.). Much like the walled gardens of late 1990s’ AOL, social media sites and their attendant mobile apps offer an experience of the web within tightly constrained and closely monitored parameters. This diminishes the vulnerability from social engineering, such as the tactics utilized with ILoveYou, which is highlighted in The Lovers.4 I am not suggesting that the latent sublime of the viral and the logic of premediation are the cause of heavy social media use. They are, however, part of a larger shift made in the name of ease and security. Jonathan Zittrain, in The Future of the Internet — And How to Stop It, notes a shift from a generative logic of computing to an appliancized logic. In generative computing, powerful personal computers are heavily configurable and can be used for a variety of purposes (Zittrain 37). Their flexibility is a source of generative power. Because of this, however, they are also vulnerable to erratic behavior and unauthorized functions. Appliancized computing, on the other hand, centers on less powerful computing devices developed for a limited range of purposes. They trade flexibility for security (Zittrain 57-9). Social networking sites function as appliancized versions of web browsing. This dichotomy between appliancized and generative computing is compatible with Grusin’s arguments regarding a shift towards securitization on the web. Drawing on Amoore and de Goede’s arguments regarding securitization as promoting frictionless movement of bodies across borders, Grusin notes that the premediation of securitization operates by ensuring that there is enough data to analyze to prevent another shock such as that of 9/11 (125-6). The latent sublime of the viral structure and the premediation of antivirus software subtly reinforce the low level of anxiety regarding Internet usage that ventures beyond the walls of the garden. This corresponds with heavy social media usage, thus reinforcing the tendency to limit one’s online interactions to vetted platforms that are a major source of behavior for analysis and data for marketing. Thus the premediation of antivirus software affects the present and future in that it reinforces a wider logic of securitization.
The Lovers shows us the potential breakdown that results from allowing the viral to operate unimpeded, while antivirus software implements securitization in the name of the health of the system. I use the term “health” carefully, with the intent of invoking the biological. Our encounter with the algorithmic virus is unavoidably framed through our understanding of the biological, a relationship in which Jussi Parikka suggests the biological tends to be conceptually primary (120).5 In a refiguring of this relation, a recent flurry of epidemiological projects and apps have arisen that attempt to manage sublime latency by framing the biological through the digital. Though there are many different projects, the next section will focus on the specific strategies of three examples, each of which uses a different form of data capture. Google’s Flu Trends6 first came to prominence in 2008 and much has been made of its big data and algorithmic approach to early detection. Flu Trends uses information from regional activity related to search terms that the developers have determined typically increase in correlation to surges in flu infections (sec. How does this work?). On October 31, 2014, Google announced that in order to improve accuracy, they now also take “official CDC flu data into account as the flu season progresses” (Google Research).7 FluNearYou, a website and mobile application, relies on crowdsourced data by soliciting weekly user reports of flu symptoms and the dates on which they were experienced. In an act of anticipation, the user is sent a weekly email each Monday that reminds them that it is time to report. The subject line of the email, “How are you feeling?” is reminiscent of the social engineering utilized in the ILoveYou virus. The subject line is an act of affective anticipation by the system in that it anticipates the possibility of a response. Users can select “I have no symptoms to report” or select checkboxes for individual symptoms. In an eerie “little brother” twist, users are also invited to report symptoms on behalf of other household members (fig. 3). If a user signs on to the mobile app before submitting their report for the week, a flashing blue arrow sits at the top of the window, inviting them to report and “Add Household Members.” Sickweather, a website, mobile app, and Facebook widget, combines the two approaches. Data is harvested from mentions of illness or symptoms on social media and symptoms are directly reported by users through the mobile app. Sickweather’s tracking extends beyond the flu to include twenty three different symptoms and illnesses, from allergies to chicken pox, to whooping cough.8
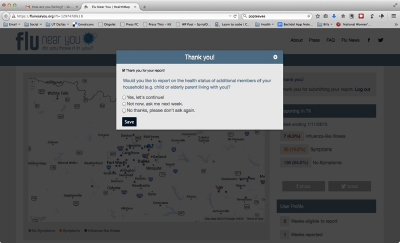
Fig. 3 Screenshot of FluNearYou’s “little brother” strategy.
The data used by these projects is the basis for the immediacy and hypermediacy associated with the logic of premediation. There is an immediacy in the unconstrained connectivity of data sources (Grusin 2), which in this case means harvesting data from different kinds of social actions and presenting them as texts algorithmically legible for the same strategy of premediation. In the case of Flu Trends and FluNearYou, searches and user reports are presented alongside, or in combination with, data from the CDC. These combine to create virtual viral futures, despite differences in the ways we might interpret these various kinds of data. When users engage in Google searches and social media status updates about illnesses, the data from which is harvested, everyday user actions are aggregated, quantified, and operationalized via algorithmic operatives similar to those in antivirus software. The immediacy of these multiple data sources creates affective feedback loops in which the user’s pleasurable everyday actions are reinscribed as contributions to the production of premediated viral futures. The logic of antiviral premediation requires the contribution of the user as a responsible producer, of both data and viral futures. The user then acts as a responsible consumer by using the websites and apps that are built upon their own data. The responsible Internet subject is produced by everyday actions of using the Internet, which makes legible the risk of infection inherent in social contact and movement through social spaces.9 The feedback loops of antiviral premediation create both the pleasure of production and the anxiety of consumption.
These are practices of data harvesting in which the data from some primary activity is reinscribed for a secondary purpose. These projects also invite more active contributions through pleasurable practices of hypermediacy, distributing one’s identity across multiple sites (Grusin 3), by borrowing strategies from other social media sites. The self-reporting and tracking of FluNearYou and Sickweather incorporate familiar practices of data tracking and the quantified self. There is a sense in which the “report” is analogous to the “status update,” and the location tracking of reports calls to mind geo-locational “check ins.” Sickweather includes “share” buttons for Facebook and Twitter, asserting its identity as a social networking site. It uses visual strategies to further this effect. The bright blue colors of the logo and the whimsical cloud shapes that indicate an illness report bear striking similarity to the design aesthetic of Twitter. The FluNearYou report card (app) and user profile (website) prominently display user reporting stats, aligning this with game play and the “achievement unlocked” statuses of games, which are often used to report among social networks. This reporting is an anticipatory act that extends into a future in which additional reports will be made and counted.
Perhaps the strongest reference to the pleasurable participation of social networking sites is in the rhetoric regarding user agency. Sickweather frames participation as giving the individual a voice. The callouts on the clouds layer the signifier of a speech bubble onto the “weather” markers and remind us that these reference user-produced information. The screen full of cloud callouts may be read as very “stormy” (filled with incidents) and as very “loud” (a cacophony of reporting voices) (fig. 4). Language used on the website supports this foregrounding of the individual: “Your voice can now be heard […] Raise your thermometer and be counted!” (sec. About). When Sickweather exhorts users to be counted and heard and FluNearYou asserts on their Facebook page that they are “putting the public back in public health,” the user is invited to join forces with the algorithmic operative to combat viral futures. The rhetoric suggests that the user is empowered, informed, and performing good citizenship through the act of self-reporting. This may seem empowering and one possible reading is that these apps draw on the participatory strengths of the web. However, this is the strategy of governmentality in control society that deploys the logic of premediation (Grusin 75-7). The user provides data to feed the proprietary algorithm that, by the rights of entrepreneurialism, maintains opacity with regard to how the data is acted upon and made legible to the public. This grants the power over the data to the project developers and governmental and corporate entities with whom the developers partner.
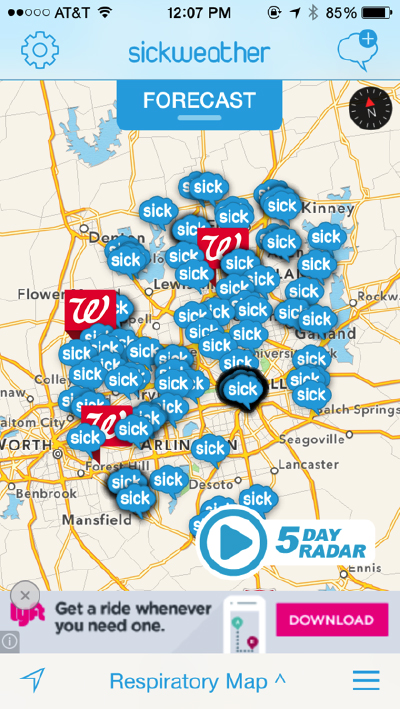
Fig. 4 Screencapture of Sickweather’s stormy cacophony.
Each of these projects justifies its data collection efforts based on a desire to make the latent sublime in the future visible and to impact public health, though the nuances of the stated intention varies: early detection (Flu Trends), preparedness (FluNearYou), and forecasting (Sickweather). The very name of Sickweather focuses on the future. The app’s name and its offering of “forecasts” for any given city reference practices of meteorological forecasting, which also attempt to make visible that which is invisible in order to lend a sense of control over the unauthorized. Sickweather’s “5 Day Radar” and multiple references to the Doppler radar reinforce the associations with weather forecasting. However, when a user launches the “5 Day Radar,” they are presented with an animated heat map of the reports for the past five days. While the name of the feature does not make an explicit claim regarding the future, the future is nonetheless invoked. Sickweather is not alone in this respect. In all of these projects, the data and visualizations stop short of the future and instead estimate or represent reports of current activity. Despite this, the logic of premediated viral futures still functions prominently. As Kirsten Ostherr notes in Cinematic Prophylaxis, “the impossibility of ascertaining the precise location of the virus until after the fact makes the threat of a new outbreak seem ever present” (ch. 1). The sublime latency of the viral suggests that based on the reporting of current activity, users can (and should) project multiple virtual viral future scenarios for themselves. Each project utilizes affective methods of representation that act as a springboard for premediation.
Flu Trends loads a choropleth map of the globe with twenty-five countries color coded according to the estimated rate of infection. The user can select a country, and the app will zoom in to that map, divided into color coded regions. In the U.S. the regions are states and the user can also zoom in to experimental data for major cities (fig. 5).10 The project has been critiqued for overestimating the rate of infection when compared to reports from the CDC and for failing to account for the way that the data might shift as a result of user actions or Google’s modifications of their own search tools (Lazar et al.). However, Matt Mohebbi, one the co-creators of Flu Trends, asserts that the tool was never intended to function as the sole predictor of infection (Lohr par. 7). Though Flu Trends may be imperfect at prediction, it functions perfectly at premediation, because it values speed over accuracy. The FAQ page boasts, “the system provides users and public health officials with near real-time estimates of flu activity in their region. Traditional surveillance reports come directly from doctors and other health service professionals, sometimes with a delay of up to 1-2 weeks.” Although the accuracy may be off, the tool algorithmically and efficiently paints a picture of estimated infection on a daily basis, providing repetition of premediated futures.
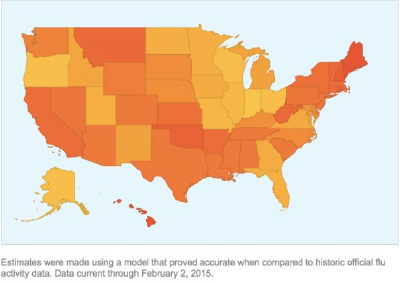
Fig. 5. Flu Trends choropleth map of the United States
FluNearYou also employs a color coded map, but this map allows the user to drill down a bit further into its data. Both the app and website load a map that is centered on an approximately 12-mile radius around the user’s location. The map is populated with colored circles that seem to appear one per postal code and are colored according to the most severe report in that area: red (Influenza-like Illness), orange (Symptoms), and blue (No Symptoms). The user can click on each dot to see the city, zip code, and breakdown of numbers reported for each category. The map in the mobile app includes a “meter:” a half circle with color coded zones ranging from “low” to “high,” and a needle that points to the appropriate threat level. This type of meter is recognizable as a form similar to an analog speedometer or RPM meter, across which the needle can move quickly (Fig. 6). In FluNearYou, if the user moves to a new location on the map, the needle bounces around before stopping in one spot. This movement of the needle is almost entirely premediation given that the rating of the “threat level” is on a state-by-state basis. Given the default zoom level, most moves on the map result in the needle bouncing around before returning to its original location. The needle bouncing around the meter is an anticipatory act that the rating could swing higher (or lower) in some virtual viral future. Premediated anxiety is reinforced by the tagline on the website, “Do you have it in you?” This is simultaneously a paranoia-inducing reference to the sublime latency of the flu virus and a challenge to the user to determine whether they “have it in them” (i.e have what it takes) to be a responsible reporting citizen. The user reports are always for the week prior so although the website invites users to “see flu activity in your area” (sec. About), the information is always slightly outdated. It is also always in the process of actualizing. Emails go out to users on Mondays asking them to report their symptoms for the past week. The data resets each week rather than showing a rolling seven day period (fig. 6 and fig. 7). Thus the data points accumulate as more people respond to the reminder emails throughout the week. Though users may be able to report for previous time periods, the site only displays the previous 7-day period. However, this data lag does not matter in the logic of premediation and the availability of more fine-grained data for user analysis increases the appearance of scientific validity.
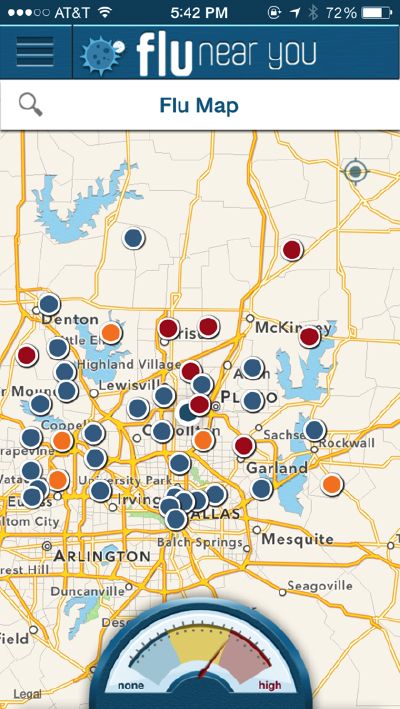
Fig. 6 FluNearYou at 6:42 PM EST on a Sunday.
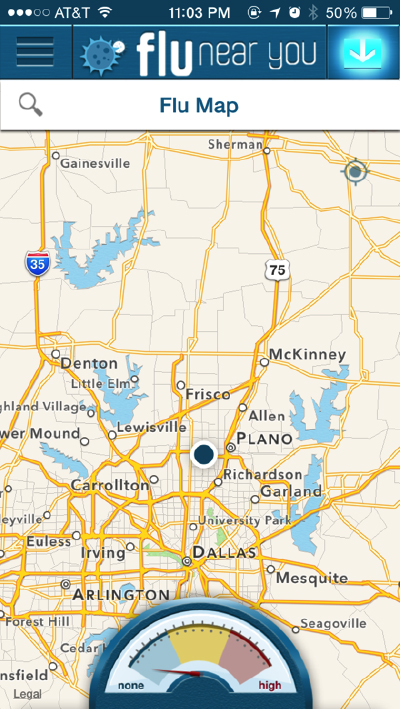
Fig. 7. FluNearYou just over 5 hours after fig. 6 at 12:03AM EST on Monday.
Sickweather offers even more “accurate” data and prioritizes use of the mobile app. There is a web-based “Live Map,” but it is not featured on the home page and its functionality is limited. When the mobile app first opens, information is clearly presented in layers. An individualized text-based forecast sits over a map of the U.S. that zooms in to the user location with an approximate seven-mile radius. The forecast can be “swiped” away using a familiar touchscreen gesture, fully revealing the map. Illness reports are indicated with whimsical, bright blue, cloud-shaped callouts. When a cloud marker is touched, a box pops up with further information, including a link to an explanation of the particular malady. I was unable to locate any pop-up markers that read anything other than “[#] Days Ago. [Illness] reported.” This text suggests that the cloud is the result of a user reported condition, though it is unclear whether the app counts data harvested from a social media mention as a “report.” The callouts contrast sharply with red “flag” markers showing the locations of Walgreens drug stores. As the user moves around the map, blue callouts “rain” from the top of the screen in a steady stream and land on the appropriate spot on the map. The more reports, the more streams falling and callouts piling up. Multiple reports from one area are layered and show a dark dropshadow outline that increases in size according to the number of reports contained therein. As the user zooms in, the layered callouts may separate and spread as the map becomes more detailed, or they may retain their dropshadow if they originate from the same exact location. The accuracy of the location is quite precise and allows the user to zoom in to see where a report originated, down to the location of a building on a block. Though the map itself is very detailed and precise in pinpointing the location of a report, there is ambiguity regarding the source of the report.
All of these apps draw on the familiar signifier of the epidemiological map that addresses the sublime latency of the virus by making it visible. As a practice that truly began in 1854 with John Snow’s map of the Broad Street cholera outbreak, mapping has a long history in epidemiology (Johnson). This visual motif has also been used as an awareness tool in public health campaigns and appears in many popular culture texts,11 ranging from games to films. Kirsten Ostherr suggests that the use of animated maps in early public health education films trained audiences to imagine germs that were not visible (ch. Introduction). The prevalence of this motif in U.S. popular culture suggests that this has become a recognizable strategy through which audiences may imagine an apocalyptic scenario. In fact, the motif was parodied by The Simpsons in the 2002 episode, “TreeHouse of Horror XIII.” In the segment, “Send in the Clones,” the damage of out-of-control cloning is projected with an incident map of the U.S. using Homer heads to symbolize each clone, which are projected to engulf the country by the next day. The parody of the map in The Simpsons suggests that the disease map is culturally legible for U.S. audiences. Each of the maps in the antiviral projects discussed here shows the past or stops in the present, just short of forecasting the future. However, the sublime latency of the viral and the familiarity of the disease map work together to create a scenario of anticipation which invites the user to imagine virtual futures and complete the work of premediation. The logic of premediation is so strong that the app need only lay the groundwork and the user can imagine the virtual viral futures.
One of the subtitles on Sickweather’s website makes this logic explicit: “Avoid the Plague with Alerts.” The language of “the Plague” is used to hyperbolic effect and the section goes on to vaguely refer to Sickweather’s “patent pending process,” emphasizing the proactive mode enabled by the app, rather than “waiting for the news to report outbreaks.” The alerts are email messages or notifications via the mobile app. Like the update notices of the antivirus software, the Sickweather mobile notifications function as ghostly reminders of the sublime latency of the viral, reinforcing processes of premediation set into place by the software. The app notifications shift depending on user location and will appear any time a user is near a report of any of the twenty-three available illnesses. Like the pop up notices of antivirus software, these notices are embedded in the everyday. They appear alongside notification from other apps as one goes about one’s business (fig. 8). A user might be working at a desk or driving down the street when the specter appears: “Attention! You’re near a stomach virus report.” But “near” in this case is information poor. How near? This repeats a problem found on the map: presumably the person with the virus has not stayed in one location since giving the report. The report is static, whereas people and germs are dynamic. Thus the likelihood that an alert will actually help someone “avoid the plague” is quite low. Once again, accurate predictions are not the goal. The real effect of the Sickweather notices is to reinforce the logic of premediation and promote a constant low level of anxiety.
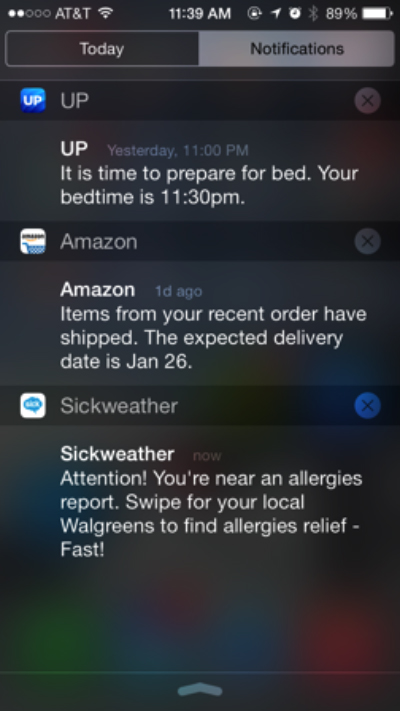
Fig. 8 Sickweather mobile alerts, directing the user to a Walgreens; visible alongside other mobile notifications
The desired outcome of the notice is made explicit in the addendum that appears in some notifications, “Attention! You’re near an allergies report. Swipe for your local Walgreens to find allergies [sic] relief - Fast!” Sickweather and Walgreens attempt to capitalize on the attention forced by the spectral mobile notification. In addition, the location of Walgreens is foregrounded on Sickweather’s maps. The red flags marking the locations of Walgreens drug stores are a stark contrast to the bright blue clouds and the muted tones of the map. On the mobile app, the flags appear a split second prior to the cloud shaped markers “raining” down. In addition, third party ads for a variety of products and services appear as a banner at the bottom of the map. The economic valence of the app is reinforced by the way it is situated as a high tech and entrepreneurial product. The “Avoid the Plague” section of text is situated on the homepage as part of a site-width image-text banner (fig. 9). The text sits next to an image that depicts a white hand holding an iPhone 5 or 5s. The text and this image are superimposed over a slightly out-of-focus background image, which shows two white men, facing the camera, sitting at a table in a swanky looking conference room. These images, coupled with the reference to the patenting of Sickweather’s algorithms situate the app alongside other familiar social networking apps that operate according to a similar economic model in which attention and data are monetized. Though Flu Trends and FluNearYou do not contain advertising, they still capitalize on the production of good citizens who engage in habitual searching, updating, and self-reporting. Flu Trends doubly capitalizes on user search habits since Google’s primary economic model monetizes search and their reputation stands to benefit from this secondary interpretation of user data. Like antivirus software, illness forecasting apps have a capitalist motivation to extend their sociotechnical networks into the future.
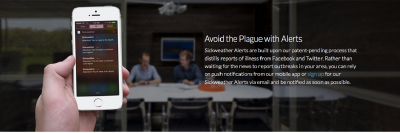
Fig. 9 Sickweather image-text
Just as the premediation enacted by antivirus software affects the present by shaping habits in good internet citizens who use the internet within safely prescribed, economically sanctioned bounds, the illness forecasting apps affect the present by encouraging good public citizens who voluntarily donate their data and who self-report on themselves and members of their households. Though Flu Trends does not operate on a model of self reporting, it does emphasize its mission of social good in order to make a compelling case for sharing one’s location in one’s internet browser in order to aid in early detection. In reading the parallels between antivirus software and social illness forecasting apps, we may group them together as antiviral technologies. Antiviral technologies respond to anxieties produced by the sublime latency of the viral structure. They deploy the logic of premediation, including immediacy, hypermediacy, and anticipation, which succeed because they are repeatedly embedded in the everyday. Though the stated purpose of antiviral technologies is to prevent infection and alleviate anxiety, the underlying logics of capital and securitization are the motivating force that allow them to impact the present and extend their sociotechnical networks into the future.
When the digital virus first appeared on the scene, it was often discussed using the biological as a metaphor. Jussi Parikka has argued that the relationship was beyond metaphorical. He suggests that the digital virus is becoming-biological and that ultimately the biological deterritorializes and reterritorializes across different texts and contexts (121). We see this clearly in antivirus software: in representations like the epidemic map of the ESG MalwareTracker, in language regarding the “health” of one’s system, and so on. This is neither a unidirectional, nor a teleological process. In the case of Flu Trends, Flu Near You, and Sickweather, the computational feeds back into the biological in a recursive process of becoming. The eco-poetics of the viral, which is a logic of premediation in response to the sublime latency of the bio/digital virus, can be located neither firmly in the biological, nor in the computational, though it is always grounded in capital and security.
Sneha Solanki’s installation artwork The Lovers is a deformance of this poetics. Absent premediation, the work refuses capital and security. Solanki uses found poetry and a found virus to create the installation that celebrates transience and the play between biological and digital. The digital virus, written by a dark hero, transmitted via love poems, between anthropomorphized computers, foregrounds the role of the human in even the most digital of contagions. The installation does not try to assuage the viewer’s anxiety and instead allows for the corruption of both systems. In the world of The Lovers, the antiviral simply does not exist. Instead, the viewer is invited to deeply contemplate the breakdown and witness processes of deterritorialization and reterritorialization. In drawing parallels between the machine and human operating system, The Lovers suggests a certain fragility about human communication and relationships, while simultaneously locating the digital in the human. The work functions by turning toward the anxiety of the latent sublime and allowing uncertainty and instability to unfold.
In contrast, antiviral technologies situate premediation as an “affective prophylactic” (Grusin 46). They deploy algorithmic actors in response to anxieties about the viral, whether it be digital or biological. As part of a viral structure, these technologies address anxiety with a claim to stop unauthorized reproduction. In fact, they reproduce themselves. The premediation of antivirus software ensures the need for expanded suites of security software and reinforces conservative habits of Internet usage that produce legible data. The premediation of flu forecasting software capitalizes on two of the largest commodities in global capitalism: attention and data. The effect of which is a constant low level of anxiety that produces responsible citizens and remediates future affective states. In addition, both kinds of antiviral technology extend sociotechnical networks into the future, thereby ensuring the continued health of systems of capital and securitization.
Works Cited
Acton, Eliza. “Where, oh ! where, on his restless wing.” Online Archive of California. Web. 22 Dec. 2014.
Anonymous. “Virus Analysis 2: Commander Bomber.” Virus Bulletin. Dec. 1992: 10 - 11. PDF. 22 Dec. 2014.
Batchelder, Dennis, et al. Microsoft Security Intelligence Report. Vol 17. Microsoft Corporation, n.d. PDF. 07 Jan. 2015.
Bennahum, David S. “Heart of Darkness.” Wired. 5.11. Wired.com, Nov. 1997. Web. 22 Dec. 2014.
Broida, Rick. “I Don’t Use Antivirus Software. Am I Nuts?” CNET Security. CNET.com, 25 Jun. 2014. Web. 07 Jan. 2015.
Brownstein, John. FluNearYou. Vers. 3.9.5. HealthMap, 31 Oct. 2014. iPhone Application. 23 Jan. 2015.
Burke, Edmund. A Philosophical Enquiry into the Origin of our Ideas of the Sublime and the Beautiful. Ed. Adam Phillips. New York: Oxford UP, 1998.
Burns, Robert. “A Red, Red Rose.” Poetry Foundation. Web. 22 Dec. 2014.
Computer Incident Advisory Capability (CIAC). “VIRS0245.TXT” CIAC, n.d.
Duggan, Maeve et al. Social Media Update 2014. Pew Internet and American Life Project, 9 Jan. 2015. Web. 20 Jan. 2015.
Enigma Software. ESG MalwareTracker. Web. 07 Jan. 2015.
Flunearyou.org. Boston Children’s Hospital, American Public Health Association, and The Skoll Global Threats Fund, n.d. Web. 07 Jan. 2015.
Fox, Susannah. Spyware: The Threat of Unwanted Software Programs is Changing the Way People use the Internet. Pew Internet and American Life Project, Jul. 2005. PDF. 07 Jan. 2015.
Fuller, Matthew. Media Ecologies: Materialist Energies in Art and Technoculture. Cambridge: MIT Press, 2005. Print.
Google. Flu Trends. Google Inc, 2011. Web. 07 Jan. 2015.
Google Research. “Google Flu Trends Gets a Brand New Engine.” Googleresearch.blogspot.com, 31 Oct. 2014. Web. 07 Jan. 2015.
Gordon, Sarah. “Inside the Mind of Dark Avenger.” VXheaven.org, n.d. Web. 22 Dec. 2014.
Grusin, Richard. Premediation: Affect and Mediality After 9/11. New York: Palgrave Mcmillan, 2010. Print.
Johnson, Steven. The Ghost Map: The Story of London’s Most Terrifying Epidemic - and How It Changed Science, Cities, and the Modern World. New York: Riverhead Trade, 2007. Print.
Kaspersky Global Research Team. Kaspersky Security Bulletin 2014. Kaspersky Labs, 8 Dec. 2014. PDF. 22 Dec. 2014.
Kohntark. “Sara Gordon v Kohntark Part I: Sara(h?) Gordon AND THE DARK AVENGER SCAM.” Phrack Magazine. 4.44. File 11. Phrack.org, 17 Nov. 1993. Web. 22 Dec. 2014.
Lambert, Patrick. “New Controversy on the Effectiveness of Antivirus Software.” TechRepublic. CBS Interactive, 20 Jan. 2013. Web. 07 Jan. 2015.
Lazer, David, et al. “The Parable of Google Flu: Traps in Big Data Analysis.” Science. Vol 343. 24 Mar. 2014: 1203-5. PDF. 07 Jan. 2015.
Lohr, Steve. “Google Flu Trends: The Limits of Big Data.” Bits. The New York Times Company, 28 Mar. 2014. Web. 07 Jan. 2015.
Martin, Brian, ed. “ciacdb.txt-Virus-Database-11-93.” Attrition.org, n.d. Web. 22 Dec. 2014.
Newman, Lily Hay. “Symantec Executive Says Antivirus Is Dead.” Slate Future Tense. Slate.com, 6 May, 2014. Web. 07 Jan. 2015.
Ostherr, Kirsten. Cinematic Prophylaxis: Globalization and Contagion in the Discourse of World Health. Durham: Duke UP, 2005. Kindle file.
Parikka, Jussi. Digital Contagions: A Media Archaeology of Computer Viruses. New York: Peter Lang, 2007. Print.
Seltzer, Larry. “‘I Love You’ Virus Turns Ten: What Have We Learned?” PC Mag Digital Edition. Ziff Davis LLC, 28 April 2010. Web. 22 Dec. 2014.
Sickweather.com Sickweather LLC, n.d. Web. 07 Jan. 2015.
Sickweather, LLC. Sickweather. Vers. 2.4.2. Sickweather LLC, 09 Jan. 2015. iPhone Application. 23 Jan. 2015.
Sunet.se “virusdb.txt” Unknown, n.d. Web. 22 Dec. 2014.
Szor, Peter. The Art of Computer Virus Research and Defense. Boston: Addison-Wesley Professional, 2005. Ebook. 22 Dec. 2014.
“TreeHouse of Horror XIII.” The Simpsons. Fox. 14 Nov. 2002. Television.
Vigna, Giovanni. “Anti-virus isn’t Dead. It Just Can’t Keep Up.” Labs.Lastline.com Lastline Labs, 21 May 2014. Web. 07 Jan. 2015.
Zittrain, Jonathan. The Future of the Internet — And How to Stop It. New Haven: Yale UP, 2008. Print.
Footnotes
-
It may seem anachronistic to apply Burke, an 18th century philosopher, to contemporary computing practices. However, the primacy of the the body and the senses in Burke’s work accord well with Grusin’s logic of premediation, with its emphasis on affect and mediality. ↩
-
Solanki lists the following aliases for VIRS0245 as follows: “Cascade, 1704, 17Y4, 1704 B, 1704 C, Cascade A, Falling Tears, The Second Austrian Virus, Autumn, Blackjack, Falling Leaves, Cunning, Fall, Falling Letters, Herbst, Cascade YAP, YAP,Jo-Jo, Formiche.” I have been unable to locate any information that suggests that VIRS0245 is in fact an alias for the famous Cascade virus. In viewing the emulator of The Lovers, the virus in the installation seems to behave quite differently from the well-known effect of Cascade, which is to make the letters on screen “fall down” to the bottom of the screen. ↩
-
I use gender-neutral pronouns (zhe/zhim/zher) when referring to Dark Avenger because the identity of the hacker is unknown. ↩
-
Sites like Facebook do pose some risk of malware. Through links and apps, users may expose their profile and those of their contacts to nuisance posts or phishing attempts. However, the types of malware do not generally threaten the integrity of the computer itself. ↩
-
See Parikka, especially Chapter Two, for a reading of the “becoming-biological of digital culture” (120). ↩
-
For a reading of Flu Trends as a surveillance system, see Lindsay Thomas, “Pandemics of the Future: Disease Surveillance in Real Time” in Surveillance & Society 12(2): 287-200. ↩
-
The ambiguity of Google’s methodology is outside the scope of this essay but is a cause for concern that is raised by any project undertaken by organizations that are not beholden to the professional responsibilities and constraints of public health organizations. Google privileges their proprietary algorithm over transparency. ↩
-
On the page, “How Sickweather Works,” the creators assert that their patent-pending algorithm can differentiate between illness and non-illness utterances, such as the difference between “these beats are sick” and “I am sick.” The app includes symptoms such as cough or nasal congestion, as well as full-fledged illnesses. Among the possible illnesses is “man flu,” a fictional condition that refers to a putative tendency for men to exaggerate their cold symptoms. This wink and elbow-nudge from the developers situates the app within the humorous ethos of social media. ↩
-
For a reading of early U.S. public health films that establish the tension between responsibility and risk in audiences, see Ostherr’s Cinematic Prophylaxis. One key difference here would be that the irresponsible actions in which users may be spreading infection are forgiven so long as they are made available as data for interpretation. Thus the emphasis is less on responsible action than it is on responsible reporting. ↩
-
Google labels flu data as “experimental” when there is no public health or government data to consider alongside the trends in search terms. ↩
-
See Ostherr for a reading of the history of animated disease maps in the public imagination and particularly for readings of how the maps function cinematically as a marker of anxieties about communist invasion and homosexual contagion. ↩
Cite this article
Knight, Kim. "Sublime Latency and Viral Premediation" Electronic Book Review, 5 July 2015, https://electronicbookreview.com/publications/sublime-latency-and-viral-premediation/